Sender Rewriting Scheme
Sender Rewriting Scheme (SRS) is mechanism for rewriting the envelope sender of an email to an “internal” email address. This is especially useful if the gateway is configured as a forwarding mail server and the sending domain has Sender Policy Framework (SPF) enabled.
SPF allows a receiving mail server to check whether the IP address of the connecting SMTP client is authorized to use a specific sender domain. If the IP address of the connecting SMTP client is not authorized to the senders domain, the mail server might refuse to accept the email or flag the email as spam.
SPF checking can be problematic if an SMTP server forwards incoming email to another mail server. If the IP address of the forwarding mail server is not included in the SPF record of the senders domain, the SPF check fails and the mail is refused or flagged as spam.
Because the external sender domain is in general not owned by the forwarding mail server, the IP address of the forwarding mail server cannot be added to the SPF record for that domain.
There are several options to fix this problem. One option is to disable the SPF check of the receiving mail server. This however is not always doable, for example the IP address of the forwarding mail server might not be static.
A better option is to rewrite the sender of an email to a domain which is “owned” by the fowarding mail server. Because the sender is now from a domain owned by he forwarding mail server, SPF checks will succeed.
A problem with a rewritten sender address is that a bounce email will now be sent to the rewritten sender and not to the original sender. SRS takes care of this by embedding the original sender into the rewritten sender address. When the forwarding mail server receives a bounce email, the original sender can be recreated. To prevent forged bounce emails, SRS signs the rewritten email address with HMAC.
For more information on SRS, see https://en.wikipedia.org/wiki/Sender_Rewriting_Scheme
SRS Configuration
Attention
SRS by default is disabled. If you want to use SRS, please contact us.
The SRS configuration page can be opened from the main menu ()
Note
While it is possible to configure the SRS at the user or domain level, most setups only require changes at the global level.
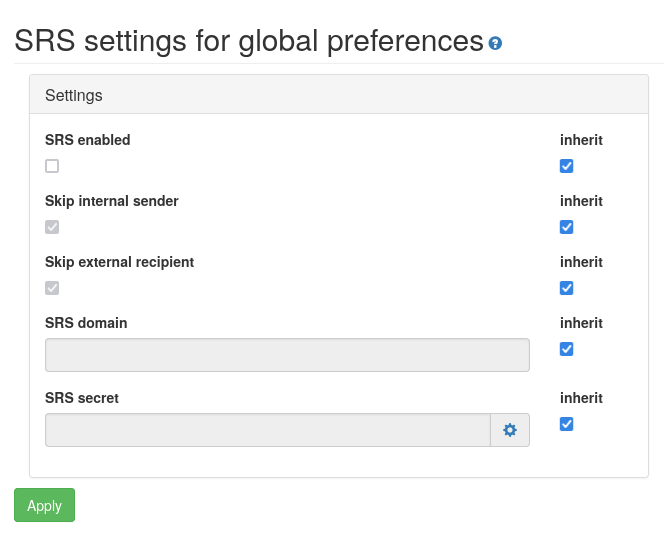
The following settings can be configured:
- SRS enabled
If set, SRS will be enabled
- Skip internal sender
If set and the sender is from an internal domain, i.e., the Locality setting of the sender is set to Internal, SRS forward rewrite will not be applied.
Note
It is advised to leave Skip internal sender to the default enabled state. In general you do not want to apply SRS for email sent from your own domains.
- Skip external recipient
If set and the recipient is from an external domain, i.e., the Locality setting of the recipient is set to External, SRS reverse rewrite will not be applied.
Note
It is advised to leave Skip external recipient to the default enabled state. In general you do not want to apply SRS for email sent to external recipients.
- SRS domain
The domain to which email addresses are rewritten to originate from this domain. This should be an internal domain, i.e., the Locality setting of the domain should be set to Internal.
- SRS secret
To prevent spoofing of fake SRS bounce emails, SRS will add a cryptographic checksum (HMAC) to every rewritten address. The allows the gateway to validate whether the rewritten address was generated by this gateway.
By clicking on the ‘cog’ icon (next to the input field), the gateway will generate a strong randomly generated secret value.
Warning
The secret value should be a cryptographically strong enough so that it cannot be guessed and should be kept secret.