Domain to domain encryption
Domain-to-domain encryption protects all email exchanged between two organizations at the domain level, so users do not need to configure anything in their mail clients. To use domain-to-domain encryption, both the sending and the receiving organization must operate an email encryption gateway that supports S/MIME or OpenPGP (PGP). Each organization also needs a valid S/MIME certificate or a PGP public key representing its domain that the other side can trust. In practice, this means the two organizations exchange and trust each other’s domain certificate (for S/MIME) or public key (for PGP) and configure their gateways to use them for all messages sent between the domains.
Before enabling domain-to-domain encryption, confirm the following:
Each organization has an email encryption gateway capable of S/MIME or PGP domain encryption.
Each organization has a current, trusted S/MIME certificate or a PGP key for its domain, and the counterpart has imported and trusted it.
The gateways are configured to apply encryption for mail routed between the specific domains.
Additional notes:
Domain-to-domain encryption is different from transport encryption (TLS). TLS protects the connection between mail servers, while S/MIME or PGP protects the message content end to end.
Subjects, headers, and some metadata may remain visible depending on gateway settings and standards; only the message body and attachments are typically encrypted. It is therefore advised to also use TLS.
Plan for certificate or key lifecycle management, including renewal, rotation, and revocation handling, and agree on a process for exchanging updates.
After setup, send a test message in both directions and verify on each gateway that encryption was applied successfully.
Tip
You can use a self-signed certificate for encryption between domains.
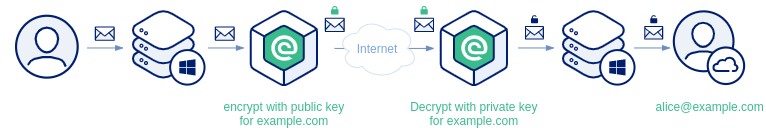
S/MIME domain to domain encryption
To enable S/MIME domain-to-domain encryption, install a certificate that includes its private key on the gateway. This certificate will represent the entire domain. Set the certificate’s email address to something that clearly identifies it as a domain certificate, for example: domain-cert@example.com.
Note
There is no official S/MIME domain certificate. In practice, any certificate can be configured for use as a domain certificate. For clarity and security, it is recommended to issue a dedicated certificate specifically for domain-to-domain encryption and include an email address that clearly indicates it should be used only for domain-to-domain encryption.
Tip
To ensure both parties are using the correct domain certificate, verify it by exchanging the certificate’s thumbprint (hash) with the other party over a trusted channel, such as a phone call. Compare the thumbprints on both sides. If they match, you can be confident the correct certificate is being used.
To enable secure connections, import the external organization’s domain certificate into the gateway.
To configure domain to domain encryption, use the following procedure:
Create (or import) a certificate with private key which will be used for domain to domain encryption. You can also use an existing certificate for your domain to domain encryption.
Import the domain certificate from the external organisation.
Make sure the domain certificate is valid. If the domain certificate is self signed, place the domain certificate on the Certificate Trust List (CTL) to make the certificate valid.
Create a domain object for the external domain ()
On the domain settings page, open the “S/MIME encryption” page and select the certificate which should be used for the domain and Save
If an email is sent to an external domain and encryption is required, it will be encrypted using that domain’s certificate.
PGP domain to domain encryption
To set up PGP domain-to-domain encryption, ensure a PGP private key is available on the gateway to act as the domain PGP key. Because this key represents the domain rather than an individual, set the key’s email address (user ID) to something that clearly indicates it is a domain key, for example: domain-cert@example.com.
The domain key of the external organisation should be imported into the gateway.
Tip
To confirm that both parties are using the correct domain key, verify the key’s thumbprint (hash) by contacting the other party directly. Each party should read their key’s thumbprint to the other and compare the values. If the thumbprints match, you can be confident that the correct domain key is in use.
To configure domain to domain encryption, use the following procedure:
Create (or import) a PGP key with private key which will be used for domain to domain encryption. You can also use an existing PGP key for your domain to domain encryption.
Import the domain PGP key from the external organisation.
Make sure the domain PGP key is valid.
Open the details page for the PGP key.
On the “Details for PGP key…” page, add the domain to the PGP key and Save
When an email is sent to an external domain and encryption is required, the message is encrypted using that domain’s PGP key.