
In EFAIL: which is vulnerable? PGP, S/MIME or your mail client?, we discussed some implications of the newly found EFAIL attack on PGP and S/MIME. We concluded that CipherMail gateway was not directly vulnerable because the gateway does not load remote content from the email. The email only gets decrypted, validated and then forwarded.
The EFAIL paper describes two types of attack. The Direct exfiltration attack and the Generic exfiltration attack.
Messages decrypted by the CipherMail gateway are not vulnerable to the Direct exfiltration attack even if you use a mail client which is vulnerable to the Direct exfiltration attack because CipherMail will always generate messages having correct MIME parts after decryption. PGP messages decrypted by CipherMail are also not vulnerable to the Generic exfiltration attack because a Modification Detection Code (MDC) is required and checked. If a message does not have the correct MDC, the message will not be decrypted (see EFAIL: which is vulnerable? PGP, S/MIME or your mail client? for more details)
S/MIME
S/MIME however is vulnerable to the Generic exfiltration attack. With the Generic exfiltration attack the attacker can insert additional content (payload) into an encrypted email without having to decrypt the email first. This by itself does not directly result in the loss of information. However, if the email is viewed on an email client which automatically downloads external content, part of the decrypted email might be uploaded to a remote system.
Generic exfiltration
We have further analyzed EFAIL and have been able to modify an S/MIME message using the described Generic exfiltration technique.
Inserting the required payload is not straightforward. Only small parts can be inserted (max 16 bytes). To insert a payload which can be used to upload the decrypted contents requires multiple blocks to be inserted. The problem with inserting blocks into the encrypted stream, is that the blocks are separated by bogus data (random plaintext). The paper describes in a clever way how the inserted payload can be optimized to make sure that the HTML parser skips the bogus data.
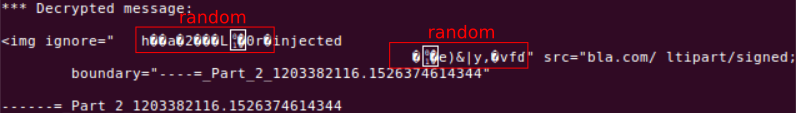
The bogus data however, can also be used to detect that an EFAIL attack has been executed. S/MIME specification (RFC 5751) requires that an S/MIME message should only contain 7-bits characters:
If a multipart/signed entity is ever to be transmitted over the standard Internet SMTP infrastructure or other transport that is constrained to 7-bit text, it MUST have transfer encoding applied so that it is represented as 7-bit text. MIME entities that are 7-bit data already need no transfer encoding. Entities such as 8-bit text and binary data can be encoded with quoted-printable or base-64 transfer encoding.
S/MIME messages containing characters outside the 7-bit range are therefore invalid. This gives us an opportunity to detect whether the EFAIL attack was used. The chances of detection can be further improved by also disallowing most control characters. in normal emails, only CR, LF and TAB will be used.
When using the CipherMail Email Encryption gateway, a spam or content filter can detect whether the decrypted email contains invalid characters and quarantine the email in such a case.
Automatic detection
We are investigating whether an automatic 8-bit character detection module can be added to the CipherMail gateway. With this module, if a decrypted email contains invalid characters, the gateway will not forward the email in decrypted form but forward it in encrypted for to an admin for further analysis.
Update
This functionality has now been implemented in the CipherMail Email Encryption Gateway. For more information see EFAIL: detection and prevention