Even though we believe that email encryption at the gateway level is the easiest way to encrypt your email1, in certain situations, desktop to desktop encryption (using Outlook for example) might still be preferred. For example the email infrastructure might be completely outsourced and regulatory requirements demand that the external company should have no access to the contents of sensitive emails.
There are various legal discovery rules requiring emails to be archived for a number of years (for example HIPAA, SEC etc.) If email is encrypted on the desktop it will automatically be archived in encrypted form. Archiving encrypted email sounds like a good idea from a security point of view. However, storing email in encrypted form might lead to some problems later in time when email has to be retrieved from the archive. To access the contents of the email, the correct private key is required to decrypt the email. A problem with that is that it is impossible to know in advance which emails need to be retrieved from archive later in time. Therefore, all private keys used for email encryption must be securely stored together with the email archive. For small organizations this might be doable. For large organizations however keeping a record of all private keys might be more problematic. Imagine a company with 10,000+ employees. If every employee gets a new certificate every year and email should be kept for 10 years, at least 100,000 keys should be stored. Even if the company manages to store all private keys, there might still be problems adhering to the required legal discovery rules.
For example searching the archive for certain content is not supported unless the archiving solution has access to all private keys and all encrypted emails are decrypted by the archiving solution. Even if the archiving solution is able to decrypt all email, decrypting and searching a 10-year-old archive of millions of emails can take a long time. Another problem is that you only know whether you have access to the correct private key if you can decrypt the message successfully. What happens if you later find out you forgot to archive some private keys? Or if some department issued their own certificates and those certificates and keys were not properly archived. If a legal order demands that you hand over certain emails, you need to be absolutely certain that you can find and decrypt those emails.
Instead of archiving encrypted email, a better solution might be to decrypt the email just before archiving. This way there is no need to keep all encryption keys for a long time (only as long as the certificate is valid) and you can be certain that all email can be read. By placing a CipherMail gateway between the email server and the archiving system, all email will be decrypted before sending it to the archiving system (see image below). This even works for email forwarded by an Exchange journaling agent (the CipherMail gateway will decrypt the attached email). All available private keys can be imported into the gateway or, if there are many private keys, private keys can be imported on demand.
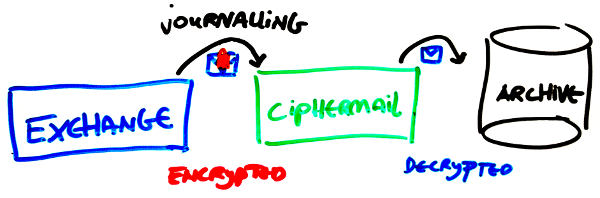
Storing all private keys on a single location can be a security issue. To securely store private keys a Hardware Security Module (HSM) is advised2. Because the decryption gateway is able to decrypt all email, access to the gateway should only be allowed to certain key personnel.
Desktop to desktop email encryption is one of the most secure ways to secure your email. Desktop email encryption however might be conflicting with the requirement to archive email in a readable and search able form. Placing an email encryption gateway before the archiving system might help to fulfill both requirements.